Attack Surface Management
Attack Surface Management
Attack Surface Management
OFFen ASM
OFFen ASM
OFFen ASM
Take control of your Shadow IT
ASM
ASM
ASM
Trusted asset management, guided by White-Hat know-how
Trusted asset management, guided by White-Hat know-how
Trusted asset management, guided by White-Hat know-how
OFFen ASM
Attack Surface Management Service
Managing countless neglected IT assets — Don’t put it off any longer
Growth is great.
But what about your growing security gaps?
Growth is great.
But what about your growing security gaps?
Cloud, remote work, and IoT are expanding your attack surface.Monitor it in real time with ASM.
Cloud, remote work, and IoT are expanding your attack surface.Monitor it in real time with ASM.
Tired of noisy alerts? See only what truly matters.
We thoroughly verify and filter issues by asset, so you can focus on what truly needs attention.
Tired of noisy alerts? See only what truly matters.
We thoroughly verify and filter issues by asset, so you can focus on what truly needs attention.
Still thinking about how to fix it? You might be missing your chance.
Tackling complex threats? White-hat experts provide timely, effective solutions.
Still thinking about how to fix it? You might be missing your chance.
Tackling complex threats? White-hat experts provide timely, effective solutions.
See all your assets at a glance,
Manage them with white-hat expertise
See all your assets at a glance,
Manage them with white-hat expertise
More
More
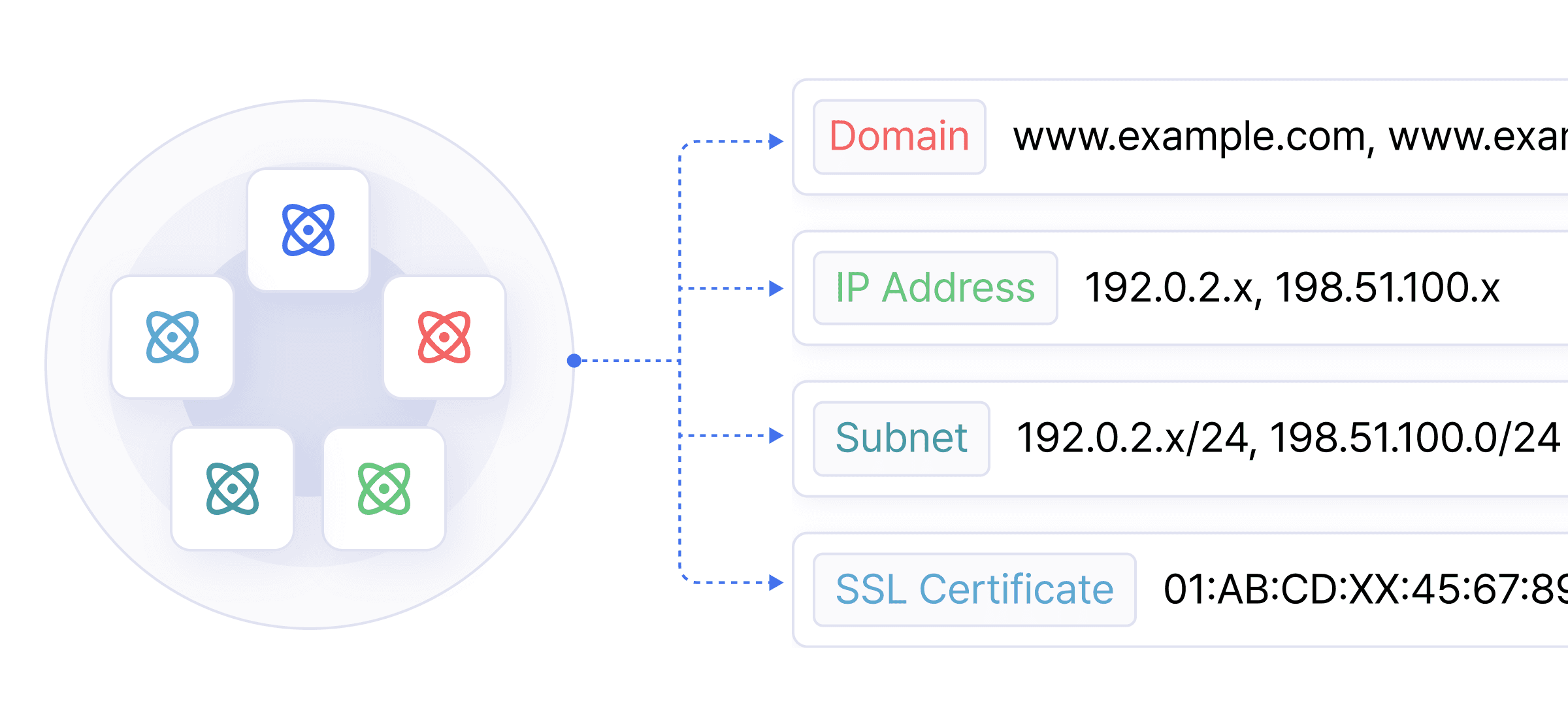
Unidentified IT assets?
We bring them all into clear view
Unidentified IT assets? We bring them all into clear view
Start with a Main domain. Discover assets instantly
Start with a Main domain. Discover assets instantly
Get a clear view of your asset mix —across all infrastructure types (Onpremise, Hosting, Cloud..)
Get a clear view of your asset mix —across all infrastructure types (Onpremise, Hosting, Cloud..)
Enhance risk management with port-level asset usage and ASN data
Enhance risk management with port-level asset usage and ASN data

Manage vulnerable attack surfaces
—more thoroughly than ever
Manage vulnerable attack surfaces
—more thoroughly than ever
From CVEs to open ports, gain full visibility of your vulnerable assets
From CVEs to open ports, gain full visibility of your vulnerable assets
Track EOL/EOS and SSL status to secure each asset at the golden time
Track EOL/EOS and SSL status to secure each asset at the golden time
Spot and fix risky DNS settings—before attackers do
Spot and fix risky DNS settings—before attackers do
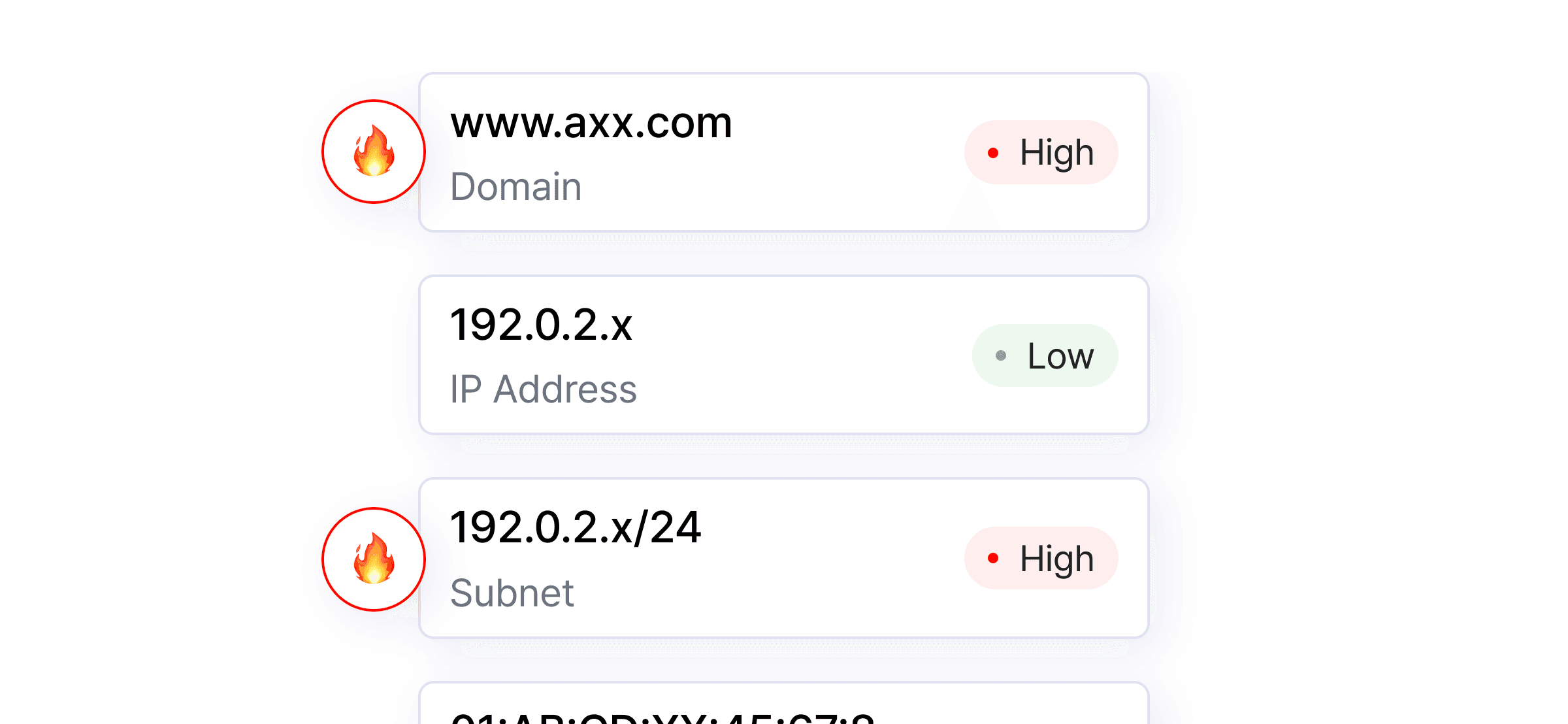
now which CVE-affected assets
need urgent attention when it matters most
now which CVE-affected assets
need urgent attention when it matters most
Focus only on actionable issues with CVSS-based risk scores
Focus only on actionable issues with CVSS-based risk scores
Evaluate risk based on vector, complexity, confidentiality, and integrity
Evaluate risk based on vector, complexity, confidentiality, and integrity
Estimate potential impact based on known CVE exploitation cases
Estimate potential impact based on known CVE exploitation cases

ENKI WhiteHat offers more than
just scans with a fully managed service
ENKI WhiteHat offers more than
just scans with a fully managed service
Built on 9 years of asset analysis experience for real problem-solving
Built on 9 years of asset analysis experience for real problem-solving
Tailored response strategies based on each organization's maturity
Tailored response strategies based on each organization's maturity
Receive expert reports with actionable findings and key asset insights
Receive expert reports with actionable findings and key asset insights
OFFen PTaaS
OFFen PTaaS
Start with OFFen ASM for visibility, extend to PTaaS for real-world testing
Start with OFFen ASM for visibility, extend to PTaaS for real-world testing
Start with OFFen ASM for visibility, extend to PTaaS for real-world testing
See more blog
See more blog
Related Blog Contents

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker
Prepare Before a Security Incident Occurs

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker
Prepare Before a Security Incident Occurs

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker



