Pre Exploit
SQL

File download

RCE
Post Exploit
Personal information leak

Server takeover

Sensitive file leak

Pre Exploit
SQL

File download

RCE
Post Exploit
Personal information leak

Server takeover

Sensitive file leak

Pre Exploit
SQL

File download

RCE
Post Exploit
Personal information leak

Server takeover

Sensitive file leak

Pre Protect
SQL

File download

RCE
Post Protect
Personal information leak

Server takeover

Sensitive file leak

Pre Protect
SQL

File download

RCE
Post Protect
Personal information leak

Server takeover

Sensitive file leak

Pre Protect
SQL

File download

RCE
Post Protect
Personal information leak

Server takeover

Sensitive file leak


Product
Product
Product
OFFen
OFFen
OFFen
An offensive integrated security platform
that leaves no blind spots at 1%
An offensive integrated security platform
that leaves no blind spots at 1%
OFFen
OFFen
OFFen
You must now prepare in advance from the attacker's perspective.
You must now prepare in advance from the attacker's perspective.
Learn more about OFFen
Learn more about OFFen
Attack Surface Management
Attack Surface Management
ASM
ASM
Penetration Testing as a Service
Penetration Testing as a Service
PTaaS
PTaaS
Experience accurate asset identification,
and thorough vulnerability examination.
Experience accurate asset identification,
and thorough vulnerability examination.
Experience continuous security without blind spots, from visualizing Shadow IT through advanced detection technologies to high-level vulnerability assessment services by white hat hackers.
Experience continuous security without blind spots, from visualizing Shadow IT through advanced detection technologies to high-level vulnerability assessment services by white hat hackers.
OFFen ASM
OFFen ASM
OFFen ASM
Reduce indiscriminate warnings,
and make judgments accurately
Learn more about ASM
Learn more about ASM

1
Asset Trustworthiness
Classify corporate-owned assets as low/medium/high based on probability and then set verification priorities.
1
Asset Trustworthiness
Classify corporate-owned assets as low/medium/high based on probability and then set verification priorities.
2
Management status
By verifying asset management status through Managed/Stopped/Owned by Others/Request for Confirmation, minimize internal confusion.
2
Management status
By verifying asset management status through Managed/Stopped/Owned by Others/Request for Confirmation, minimize internal confusion.
3
associated IP
Collect and display all IPs associated with discovered assets to understand the related network scope and relevance.
3
associated IP
Collect and display all IPs associated with discovered assets to understand the related network scope and relevance.
4
Find CVE
Automatically collect newly disclosed 1-day vulnerability information, and secure a vulnerability management system according to CVE impact analysis of existing assets
4
Find CVE
Automatically collect newly disclosed 1-day vulnerability information, and secure a vulnerability management system according to CVE impact analysis of existing assets
5
Domain Change History
Record and track domain information changes
to identify ownership and operational environment changes
5
Domain Change History
Record and track domain information changes
to identify ownership and operational environment changes
OFFen PTaaS
OFFen PTaaS
OFFen PTaaS
Professional White-Hacker
Conducts End-to-End Security Diagnosis
Learn about PTaaS
Learn about PTaaS

Understand Your Security,
Stop Getting Lost
Understand Your Security,
Stop Getting Lost
To ensure seamless security management, necessary information must be provided promptly. Gather all required status updates in one place to make the best decisions.
To ensure seamless security management, necessary information must be provided promptly. Gather all required status updates in one place to make the best decisions.
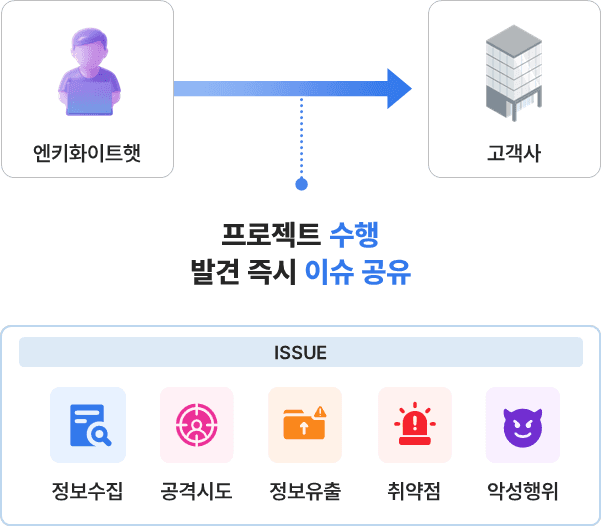
Real-time shared issues
Faster response time
Real-time shared issues
Faster response time
We classify the identified issues by type and report them immediately. The weaknesses' complexity, attack impact, and exploitability are quantified in a risk assessment to support swift and accurate responses.
We classify the identified issues by type and report them immediately. The weaknesses' complexity, attack impact, and exploitability are quantified in a risk assessment to support swift and accurate responses.

Compliance Check,
One Click is Enough.
Compliance Check,
One Click is Enough.
Easily complete in-depth verification by quickly validating patches with the PoC created by a white hacker through one-click replay, and request implementation checks with the verification request button.
Easily complete in-depth verification by quickly validating patches with the PoC created by a white hacker through one-click replay, and request implementation checks with the verification request button.
Related Blog Contents

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker
Prepare Before a Security Incident Occurs

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker
Prepare Before a Security Incident Occurs

The Beginning of Flawless Security System, From the Expertise of the No.1 White Hacker



